Migrate Azure Ad Connect To New Server
In the previous post we configured all the prerequisites for our Exchange and Office 365 hybrid environment. We now need to configure the authentication method we are going to use for users to login to Office 365 which is achieved using the Azure Active Directory Connect tool. The first time I used this tool it was fairly basic (it was called DirSync back then) but since then it has become a lot more advanced.
- Azure Ad Connect Auto Upgrade
- Migrate Azure Ad Connect To New Server Ip
- Migrate Azure Ad Connect To New Server Mac
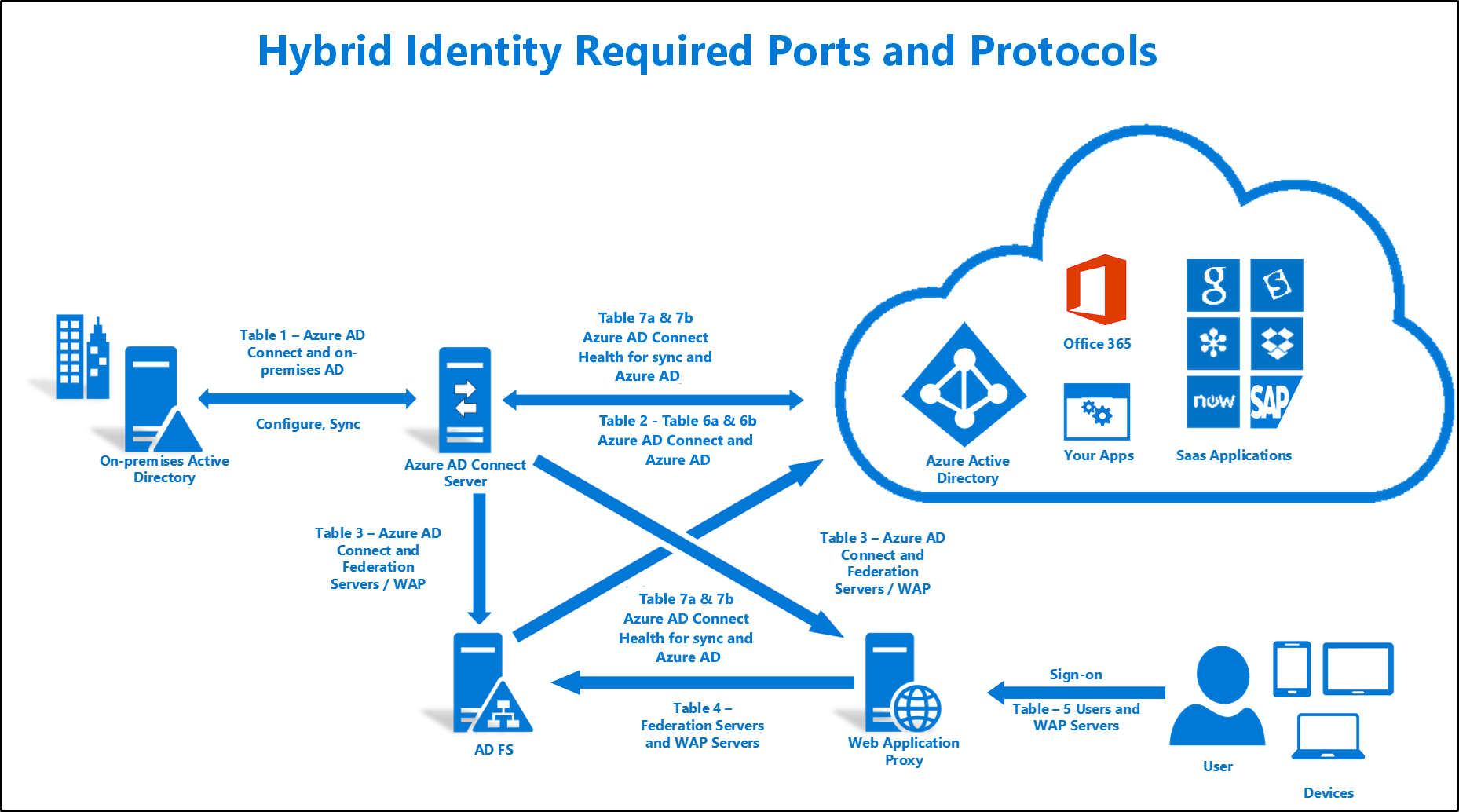
Run Azure AD Connect. That is the AzureADConnect.exe which is usually located in the Microsoft Azure Active Directory Connect folder in Program Files; Select Configure staging mode (current state: enabled), select next; Validate credentials and connect to Azure AD; Configure staging mode – un-tick; Configure and complete the change over. In this blog post, I'll be migrating Azure AD Connect (once known as 'DirSync') from an older server running Windows 2012 R2 to a newer server running Windows 2016. The new server is already a member of the domain and been prepared with any prerequisites. I've done a number of migrations of DCs in the past but can't find detailed steps on how to move Azure AD Connect and-existing settings-over to the new server once I decommission the old one. The new DC will have the same IP as the old DC, but not the same name.
We have options such as seamless single sign-on and pass-through authentication, all of which I will discuss. The AAD Connect tool also now has built in options to select for a hybrid Exchange migration that we will be using.Something I want to discuss quickly before we run through the configuration of AAD Connect is that once you enable password sync and assign licences to your users anyone can then attempt to login to them! This is a huge security risk for your company and you will immediately start to see sign-in attempts from parts of the world that you probably should not.
For that reason I will go over how to lock down Azure so that your accounts are protect from the outset and only your corporate users can login to them. Azure AD Conditional AccessBefore running the AAD Connect tool and creating Azure AD users based on our on-premise Active Directory we need to ensure that the Azure AD environment is secure. For this we can introduce a conditional access policy.Open the Azure Admin Center Azure Active Directory Conditional AccessClick on Named Locations and click New Location. Enter the name of the location and click IP ranges, then enter the IPs/ranges requiring access.Click Policies New Policy Select Assignments Users and groups and select All users.Click the Exclude tab and select Users and Groups. Click Select excluded users Select the users that you don’t want the policy to apply to.Select Cloud apps and select All cloud apps.Select Conditions and click Locations Select Any locationClick the Exclude tab and click Selected locations Select the Named location you created.Select Access controls and click Block access, then enable the policy and click Save.Now that we are happy that the Azure AD cloud environment is secured we can proceed with the installation of Azure AD Connect.
Azure AD Connect InstallationWe are now ready to proceed with the installation of Azure AD connect and assume at this stage that the following prerequisites have been completed:. mydomain.com domain verified in Office 365. Build a Windows 2016 Server and (required for PowerShell module used by AAD Connect). I chose to install this on a separate server just for AAD Connect. Article explains why not to put it on a Domain Controller.NET Framework 4.5.1 installed. Added to trusted sites. Created a service account (mine is called O365cloudsvc) in Office 365.
Check backups of all domain controllers are all ok.1. Run the installer which can be downloaded2. Select Custom Settings and under Required Components leave all unchecked and click Install3. Select Password Hash Synchronisation and check the box for Enable single sign-on. See below for notes on what the options mean.Password Hash SyncUsers are able to sign in to Microsoft cloud services, such as Office 365, using the same password they use in their on-premises network. The user’s passwords are synchronized to Azure AD as a password hash and authentication occurs in the cloud.
See Password hash synchronization for more information.Enable Single Sign onThis options is available with both password sync and Pass-through authentication and provides a single sign on experience for desktop users on the corporate network. See Single sign-on for more information.4. Connect to Azure ADOn the Connect to Azure AD screen, enter the credentials for O365cloudsvc (Global Admin). A recommendation is to use an account in the default onmicrosoft.com domain, which comes with your Azure AD directory. This account is only used to create a service account in Azure AD and is not used after the wizard has completed.5. Connect your directoriesTo connect to your Active Directory Domain Service, Azure AD Connect needs the forest name and credentials of an account with sufficient permissions. Click Add directory when you see mydomain.com.6. When prompted select the Use Existing AD account option. Use the account O365onpremsvc7.
Review the UPN domains (for us should just be mydomain.com). Then select userPrincipalName for the USER PRINCIPAL NAME.
This will be how the users will login to Office 365. So for our users this will be their primary SMTP email address.8. Leave the default options to Sync all domains and OUs. If we were only using the Exchange Online we would probably only select a subset of users. However will be using Azure Premium (included with E3 +EMS licence) so the entire Domain and all OUs should be synchronised.9. We do not need to worry about this section as we only have a single forest. We can use the default option of ‘Users are represented only once across all directories’.Select the option to ‘Let Azure manage the source anchor for me’. See below for a description of how this is done.Let Azure manage the source anchor for meSelect this option if you want Azure AD to pick the attribute for you. If you select this option, Azure AD Connect wizard applies the sourceAnchor attribute selection logic described in article section Azure AD Connect: Design concepts – Using msDS-ConsistencyGuid as sourceAnchor.
Azure Ad Connect Auto Upgrade
The wizard informs you which attribute has been picked as the Source Anchor attribute after Custom installation completes.10. Leave the default option to Synchronize all users and devices11. Select the following options from the Optional Features section:.
Migrate Azure Ad Connect To New Server Ip
Exchange Hybrid deployment. Password Synchronisation. Password WritebackSee below for a description of these features.Exchange Hybrid DeploymentThe Exchange Hybrid Deployment feature allows for the co-existence of Exchange mailboxes both on-premises and in Office 365. Azure AD Connect is synchronizing a specific set of attributes from Azure AD back into your on-premises directory.Password hash synchronization If you selected federation as the sign-in solution, then you can enable this option. Password hash synchronization can then be used as a backup option. For additional information, see Password hash synchronization.If you selected Pass-through Authentication this option can also be enabled to ensure support for legacy clients and as a backup option. For additional information, see Password hash synchronization.Password writeback (see below for more detail on SSPR)By enabling password writeback, password changes that originate in Azure AD is written back to your on-premises directory.12. Leave the default list of Azure Apps as it is and click Next, it is not recommended to change these settings:13.
We want to export all attributes so leave the default selections as they are and click Next:14. Click Next and Next again on Optional Features.15. Enabling Single sign on (SSO)Configuration involves two steps as follows:Create the necessary computer account in your on-premises Active Directory.Configure the intranet zone of the client machines to support single sign on.Enter the credentials for O365onpremsvc in the format:mydomain-ukO365onpremsvcWe next need to add two URLs to the intranet zone.
This ensures that the domain joined computer automatically sends a Kerberos ticket to Azure AD when it is connected to the corporate network.1. Open the Group Policy Management tools2. Edit the Group policy that will be applied to all users. For example, the Default Domain Policy.3. Navigate to User ConfigurationAdministrative TemplatesWindows ComponentsInternet ExplorerInternet Control PanelSecurity Page and select Site to Zone Assignment List per the image below.4. Enable the policy, and enter the following item in the dialog box.16. The next stage is to complete the Wizard.
Select to Start the synchronisation process as soon as the configuration completes. Do not enable staging mode. This completes the AAD Connect Wizard.You should now be able to open the Synchronisation Service Manager App and see the sync status:Troubleshooting Sync ErrorsIf like me you receive a sync error regarding a ‘Mailnickname’ it could be because the group being synced has one or more ‘.’ in it. I found the below on the Azure feedback portal:The Sync will occur by default every 3 hours.Some useful commands to manage AAD Connect:Import AAD Connect Module. Start-ADSyncSyncCycle -PolicyType DeltaYou should also note the below:1. Add your domain admin accounts to the ADSyncAdmins group on the server (If you don’t do this your admins wont be able to use the newly installed AAD Connect tools).2. Verify the connection Admin Azure Active Directory Azure Active Directory Azure AD Connect Check Sync StatusLater on we decided to add a single OU to our on-premise AD that would not sync with Azure AD.
Migrate Azure Ad Connect To New Server Mac
This gave us an easy way to remove items from Azure AD. To change the sync scope we had to do the below:1. Sign in to the server that is running Azure AD Connect sync by using an account that is a member of the ADSyncAdmins security group.2. Start Synchronization Service from the Start menu.3. Select Connectors, and in the Connectors list, select the Connector with the type Active Directory Domain Services. In Actions, select Properties.4. Click Configure Directory Partitions, select the domain that you want to configure, and then click Containers.5.
When you’re prompted, provide any credentials with read access to your on-premises Active Directory. It doesn’t have to be the user that is prepopulated in the dialog box.6. In the Select Containers dialog box, clear the OUs that you don’t want to synchronize with the cloud directory, and then click OK.7. When you’re done, close the Properties dialog by clicking OK.8. To complete the configuration, you need to run a Full import and a Delta sync. Force Azure AD Connect to connect to specific Domain Controllers onlyTo check which domain controller AAD Connect is currently connected to just open the Synchronization Service Manager and click Connectors.
It will list the DC that is currently used.To change this so that you can use preferred domain controllers do the following:1. Right-click the connector and click Properties2. In the properties window, go to Configure Directory Partitions and make sure to check the box next to Only use preferred domain controllers:3. In the Configure Preferred DCs window, add the domain controllers you want AAD Connect to use.

You can change the order the domain controllers are used by moving them up/down the list.4. Click OK TroubleshootingYou may encounter problem accounts or groups that complain about proxy address conflicts.You may find that some accounts are fine when queried by IDFIX but fail on a proxy address conflict.The issue in this case was as follows:You have a user account:SamAccountNameReportsUPNreports@mydomain.comSMTP Address (Proxy address)reports1@mydomain.comYou also have a distribution list:NameReports InfoSMTP Address (Proxy Address)reports@mydomain.comThese accounts have no conflicting attributes and IDFIX sees them as ok to sync. The issue is that the Reports account has a UPN that matches the email address of the Reports Info account. When syncing with Azure AD connect an SMTP address of reports@mydomain.onmicrosoft.com is created. This then causes a problem for the Reports Info group which will also create a reports@mydomain.onmicrosoft.com email address based on its current email address. The solution is to change the UPN for the Reports user account and then try and sync again.